Introduction
In our previous post, we introduced the Gordon-Loeb model as a tool to indicate how we might assign our budget, and we concluded that Risk is central to cyber security.
To progress, we establish the probability of an event by assessing Risk, a topic familiar to financiers and the IT departments of large corporations, but still hugely under-utilised by other professionals.

Without a doubt, Risk is central to cyber security and it’s best defined as ‘the probability of an event multiplied by the impact, or harm, that results from the event occurring’.
Consider your own organisation: perhaps 90% of staff have emailed an ‘unintended recipient’ within the past twelve months (it’s quite typical). We have a here a scenario which is likely to re-occur and which may, depending on the content, cause a range of effects (harm) ranging from none at all to exceptional. How we approach this matter is best based on risk modelling.
While many books have been written on the subject of risk, to summarise the key aspects, there are four approaches to every risk: you may tolerate, treat, terminate, or transfer a risk. Let’s look at what these four terms mean:
Tolerate a Risk
The risk is determined to be acceptable, perhaps because the costs associated with reducing the risk are too complex or too expensive. The risk shall be monitored.
Treat a Risk
Often referred to as mitigation, the risk is such that steps shall be taken to reduce the likelihood of the event or the severity of its impact.
Terminate a Risk
The most favoured approach, but often overlooked, is to remove the risk entirely. This might mean cancelling a system or process, or making fundamental changes to infrastructure such that the risk is no longer measurable.
Transfer a Risk
Risk transference involves the use of various forms of insurance, or the payment to third parties who are prepared to take the risk on behalf of the organisation.
Taking a Risk Based Approach
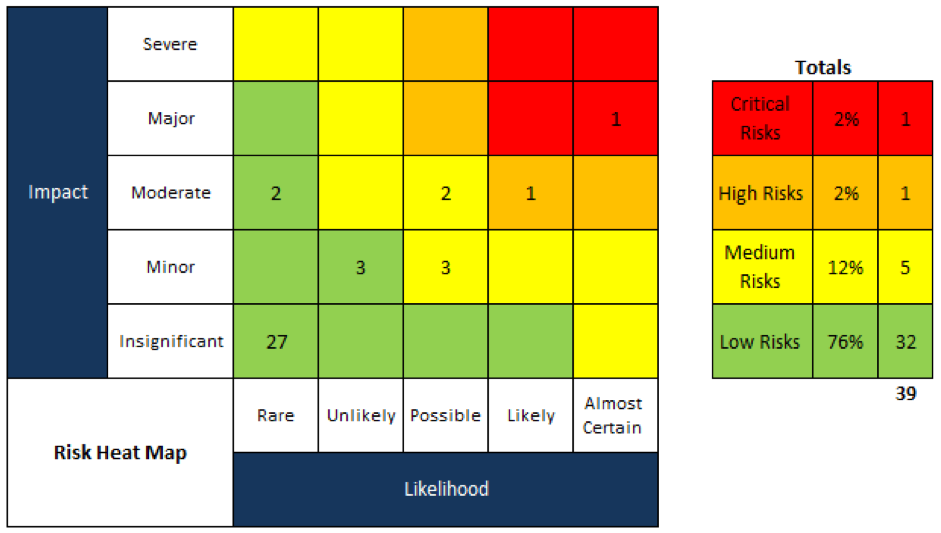
With a risk-based approach, you consider the likelihood of a re-occurrence, based upon five criteria:
- Rare
- Unlikely
- Possible
- Likely
- Almost certain
Taking the email scenario, above, we may reason that it’s ‘almost certain’ to be repeated unless there is change.
The impact will vary accordingly, and it’s ranked according to similar criteria: ‘severe’, ‘major’, ‘moderate’, or ‘minor’, or ‘insignificant’. In other words, what is the consequence upon the individual (or organisation etc.)?
Again, with the email scenario, given there are multiple departments, we might first consider emails from the sales team, and determine that an inadvertent mis-delivery would cause a low impact in terms of harm. From Human Resources, however, the disclosure of sensitive personal data could lead to both regulatory sanctions (monetary penalties), a lawsuit, and perhaps substantial public relations harm. The potential impact could be ‘major’.
By plotting the risks on a risk heat-map [see illustration], we create a visual display of the risks, and so we are guided as to where to investigate our options and, equally, where budget and resources should be expended.
The cyber security risk register drives risk management with task owners, dates for resolution, and other prompts. There’s often significant overlap with data protection legislation, and so it may prompt the execution of a DPIA.
For the Human Resources team, perhaps the cause proves to be the use of ‘auto-complete’ for email recipients? By disabling this functionality for HR users, we cause some that team a certain loss of productivity but – importantly – we have not disrupted our sales team. We have not terminated the risk, but we have mitigated it insofar as we have greatly lessened the likelihood.
For the sales team, we might commence with training. Just planting the seed that before pressing ‘send’, pause and check the recipients?
Conclusions
Risk management may be applied to IT, data protection, finance, health and safety – indeed, across the organisation – but nowhere does it assist in controlling expenditure so well as in the fields of cyber and information security.
Above all, the measurement of Risk guides effort and resources to those areas in the greatest need, and thus it protects the organisation from costly white-elephant projects which appear so bright and shiny, but which deliver perilously low value.
Have you read:
- The Relationship Between GDPR and Cyber Security
- The 5 Hidden Risks of File Sharing
- 10 Step Guide to Cyber Security
- Cyber Security vs. Printers and the IoT
- 12 Cyber Security Readiness Tips
- Cyber Security: Integrating Risk and the CIA Triad
- Why Understanding RISK is Central to Cyber Security
- A GDPR Centred Approach to Cyber Security

⏱ 5 Second Summary
Part of our Cyber Security Series
Establish the probability of an event by assessing Risk, which is the probability of an event multiplied by the impact, or harm, that results from the event occurring
Recent Posts
Humperdinck Jackman
Director of Consulting Services
Humperdinck has a 30-year career spanning Document Management Systems (DMS), data protection, Artificial Intelligence, Data Protection and Robotic Process Automation. With many articles published in print internationally, he believes the advances in office technology are such that we're entering the 4th Industrial Revolution. Now Director of Marketing and Consulting Services at Advanced UK, he's as active with clients as he is in endeavouring to write original blog articles.


