Introduction
While considerable attention is devoted to the security of the obvious – from servers to laptops – the office environment is rife with additional risks. The so-called ‘internet of things’, refers to the array of connected devices each with an IP address and a gateway to the ether. In terms of sophistication, at the top of the list is the modern office multi-functional printer (MFP).
The Power of your MFP
The 21st century MFP, can print, scan, copy, and email. The more advanced systems can deliver machine translation of documents and, surprisingly, react to voice commands. They can be configured to fetch documents from a SharePoint system, recognise when confidential documents are being printed (and alert accordingly), and so much more.61% of large enterprises admitted suffering at least one data breach through insecure printing - Quocirca
Quocirca, a leader in the field of print research, notes in their 2017 report that through a survey “61% of large enterprises admitted suffering at least one data breach through insecure printing”. Consider just a few of the risks:
- Typical office MFPs have hard disks of 2 – 320 GB – every document is stored!
- Hackers are targeting MFPs as critical infrastructure endpoints;
- Your MFP may have an embedded OS, such as MS-Windows;
- Almost all MFPs offer USB ports … instant access!
- Unprotected electronic data can be inappropriately accessed while at
- rest on the hard disk or in motion to/from the device.
- Malicious emails can be sent from an MFP with no audit trail.
Defining a Print Security Strategy
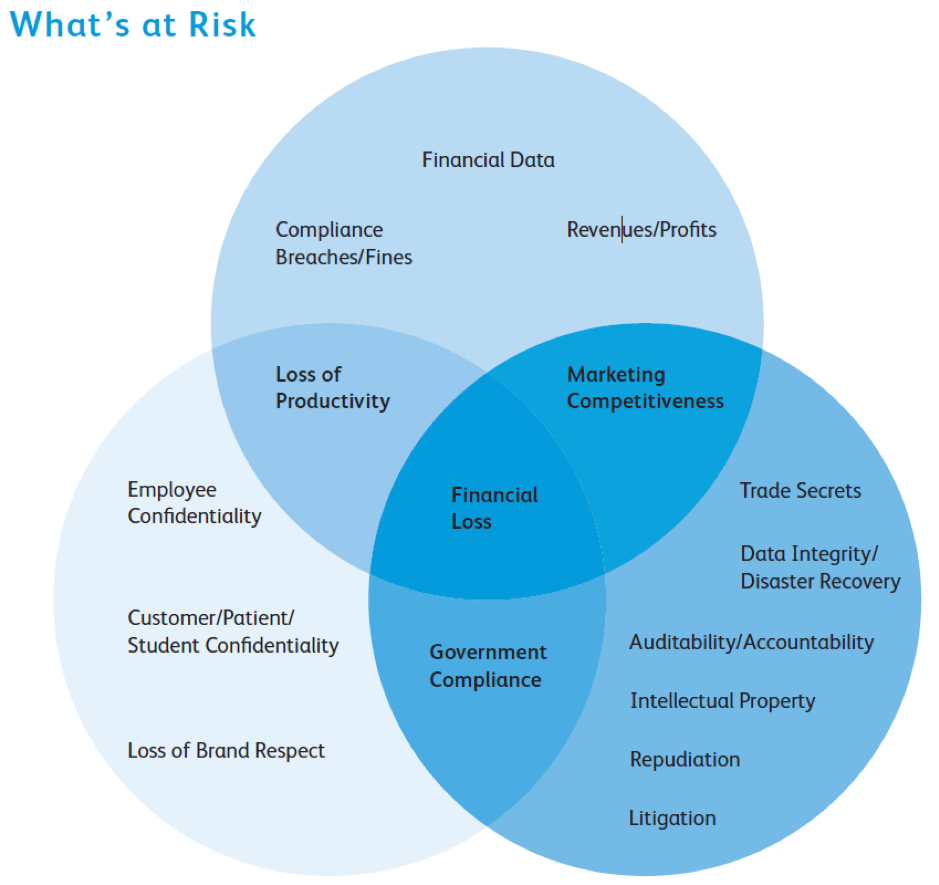
Given that data protection encompasses regulation (GDPR) and affirmative action (cyber security), and that printing represents one of the most prevalent sources of data breaches, a well-thought strategy is a commercial imperative.
Your first and most obvious vulnerability is the user interface: investigate who has physical access to your printers and their features. User authentication must be the basis for granting access such that no person can merely walk up to a device and browse data or use its functions. Only once authenticated, should the user be enabled to interact with the device, and then only according to assigned privileges.
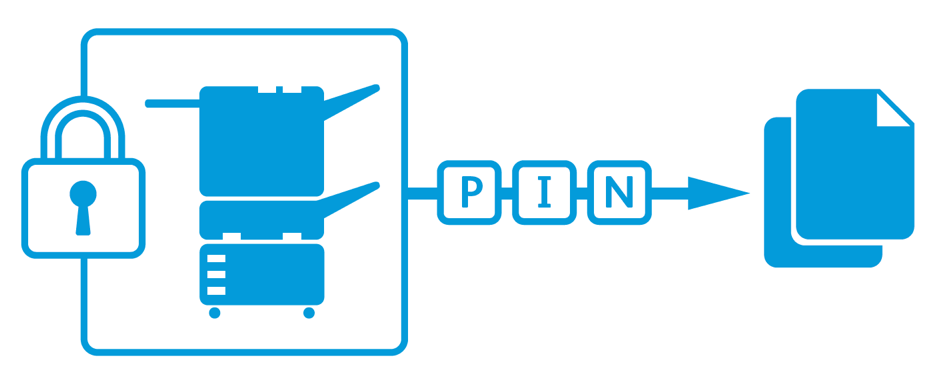
Secure printing begins with the concept of pin-release. Whether enabled by entering a pin code, or made simpler with a contactless Smart Card, this technology permits users to have appropriate access to any printer without security risks.
The printer itself should be protected with technology of appropriate strength for the data in use. Key features in this regard include:
- 256-biit AES encryption for data both in transit to the printer and at rest (i.e. the data stored on the hard disk of the device).
- Digitally signed software restrictions which prevent unauthorised software from being installed.
- Protection of data and device from malicious intrusions through the use of embedded antivirus and security such as provided by Xerox Corporation which utilises the McAfee whitelisting technology in conjunction with the Cisco® Identity Services Engine (ISE)
The full scope of suitable parameters may extend through the use of audit trails, integrated document management software and so forth. While an exploration of all such concepts is outside the scope of this document it’s worth concluding with a mention of ‘watermarking’.
Some Xerox® printers and MFPs have a Secure Watermark feature that helps prevent original printouts with sensitive information from being copied. If a document with a secure watermark is copied, the watermark image becomes visible, making it apparent that the document contains sensitive information and has been illegally duplicated.
Allied software can monitor such print jobs too, and if a document of a particular classification is printed, an alert may be sent to the document controller.
Have you read:
- The Relationship Between GDPR and Cyber Security
- The 5 Hidden Risks of File Sharing
- 10 Step Guide to Cyber Security
- Cyber Security vs. Printers and the IoT
- 12 Cyber Security Readiness Tips
- Cyber Security: Integrating Risk and the CIA Triad
- Why Understanding RISK is Central to Cyber Security
- A GDPR Centred Approach to Cyber Security

⏱ 5 Second Summary
Part of our Cyber Security Series
61% of large enterprises admitted suffering at least one data breach through insecure printing, especially because printers are IoT citizens. Secure print, follow-me print and other techniques can mitigate the risk.
Recent Posts
Humperdinck Jackman
Director of Consulting Services
Humperdinck has a 30-year career spanning Document Management Systems (DMS), data protection, Artificial Intelligence, Data Protection and Robotic Process Automation. With many articles published in print internationally, he believes the advances in office technology are such that we're entering the 4th Industrial Revolution. Now Director of Marketing and Consulting Services at Advanced UK, he's as active with clients as he is in endeavouring to write original blog articles.


