Accountability
Regardless of the size of your organisation, there’s no escaping the fact that you are to be held accountable for your processing. Further, to ensure you aren’t just ‘ticking a box’, adopt a risk-averse approach through establishing your desired outcomes, and the associated risks. Together, these are essential components to a GDPR-centric approach to cyber security
The accountability of a Data Controller brings us to the accountability principle. This requires you to be able to demonstrate that your processing is done in compliance with the GDPR. It has direct relevance to your responsibility as a data controller.
This principle requires you to implement appropriate technical and organisational measures to ensure, and be able to demonstrate, that processing of personal data is performed in accordance with the GDPR.
Appropriate technical & organisational measures?
The GDPR requires you to have a level of security that is ‘appropriate’ to the risks presented by your processing. You need to consider this in relation to the state of the art and costs of implementation, as well as the nature, scope, context and purpose of the processing. This reflects both the GDPR’s risk-based approach, and that there is no ‘one size fits all’ solution to security.
This means that what’s ‘appropriate’ for you will depend on your own circumstances, the processing you're doing, and the risks it presents. Whilst there are minimum expectations, the precise implementation of measures must be appropriate to the risks faced.
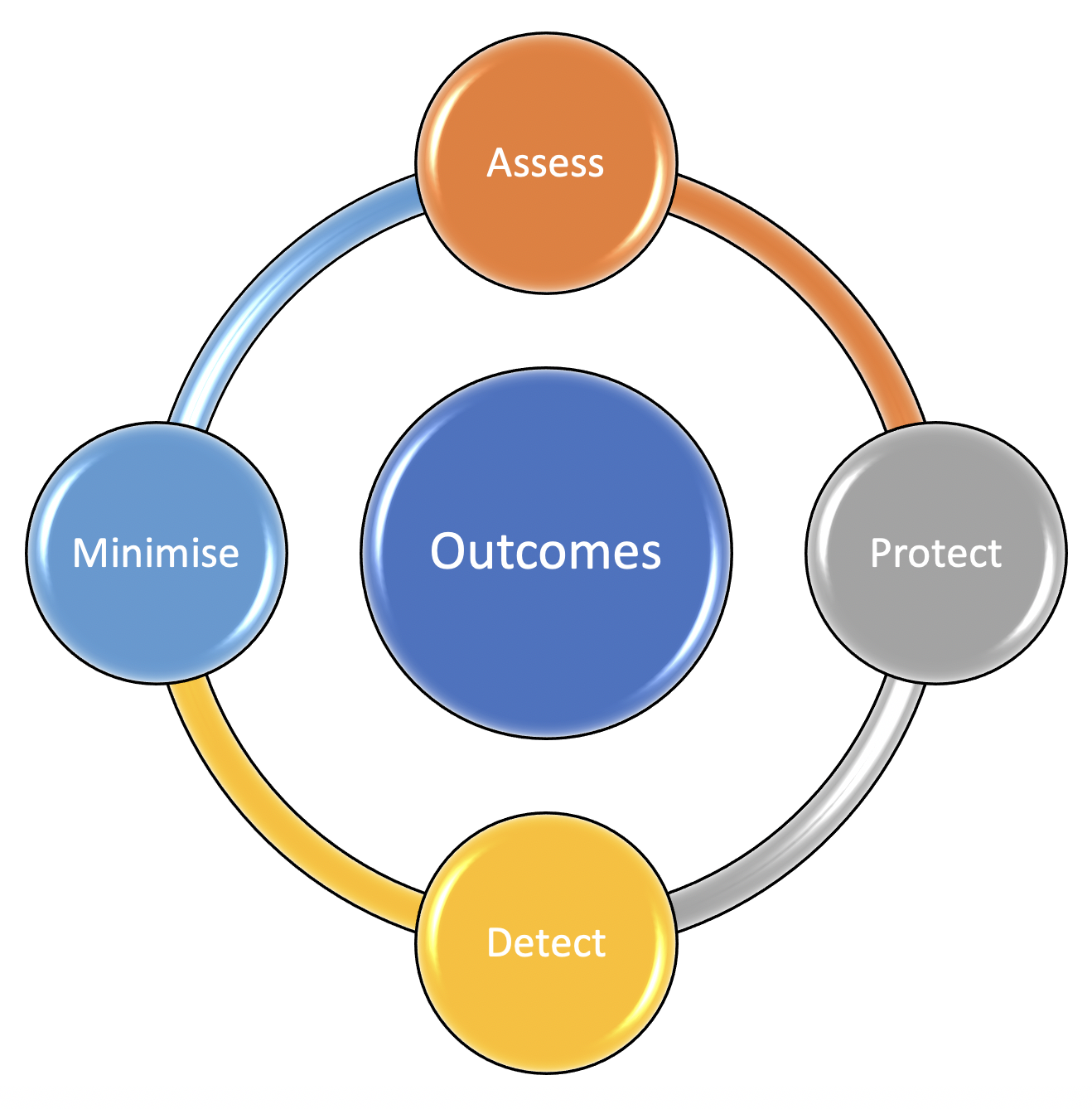
Evaluate using desired outcomes
It may seem like there is a lot of confusion as to the technical security required to comply with your data protection obligations, so we examine the desired ‘outcomes’.
There is lots of detailed guidance available, but it may not be immediately clear what you must put in place, what is simply a suggested approach, and what is relevant to you and your circumstances.
An outcomes-based approach also enables scaling to any size or complexity of organisation. The outcomes remain constant – it is how they are implemented that differs. The approach focusses upon themes of assessment, including:
- Protection
- Detection
- Minimisation
Assess: use risk management
In order to manage the security risk, your organisation must have appropriate organisational structures, policies, and processes in place to understand, assess and systematically manage the personal data.
Good information governance is your starting point. It begins with adopting appropriate data protection and information security policies and processes, and it may extend to being required to maintain records of your data processing activities.
With a basic framework of policies and procedures in place, you turn your attention to the threats posed to the data, whether these be internal, external, human or non-human. GDPR emphasises a risk-based approach to data protection and this demands you include appropriate organisational measures to make effective risk-based decisions.
The factors which come into play include:
- the state-of-the-art of the technology upon which you rely;
- the cost of implementation of enhanced technology;
- the nature, scope, context and purpose of processing;
- the impact and likelihood of the risk being realised.
Asset management is fundamental. Indeed, before you can assess a risk, you must know what personal data you process, and your lawful basis for doing so. While this is documented in the Process Register, the risks posed to the data subjects are recorded in the Risk Register. This will highlight the impact of any unauthorised or unlawful processing, accidental loss, destruction or damage to that data.
Remember too, the personal data you process should be adequate, relevant and limited to what is necessary for the purpose of the processing, and it should not be kept for longer than is necessary. By practicing data minimisation, you are inherently reducing your risk in the event of a data breach.
Your supply chain is the final part of the initial equation: because you are the data controller, you maintain legal responsibility for the personal data. So, where you’ve transferred that data to a third party, their own security – or lack of such – becomes your liability.
Protect: defend personal data from attack
Protection of personal data demands proportionate security measures to protect the data itself and the systems on which the data is being processed.
You should define, implement, communicate and enforce appropriate policies and processes that direct your overall approach to securing systems involved in the processing of personal data.
Appropriate policies include controlling access rights so to limit data access to only users who are authorised. Equally, there must be an active program to prevent users who might have administrative rights to the systems from using those administrative rights for routine tasks.
Maintaining centralised records of access rights is paramount, as is careful authentication of users with the most privileged access. From here, limiting permissions is logical, as is maintaining audit trails and logs to record user actions.
Given that passwords represent the single most common failure, the password policy must be robust and enforced, coupled with an absolute and immediate suspension of accounts of staff who have changed roles or even left the organisation altogether.
Addressing data security includes considering fresh technical measures to further protect data. This might include the use of encryption technologies to render stolen data unusable. Remember too, live emails and backup data sets may also be encrypted.
Your system security will extend into the assessment and monitoring of a wide range of both procedural and organisational measures to further protect your data from a cyber attack.
Such measures might include limiting (or even prohibiting) the use of removable media, ensuring that all software is fully supported with updates from the manufacturer, and ensuring that all systems and devices are properly configured with anti-malware and anti-virus software.
Network penetration testing is used to assess the weaknesses of your network and, despite the assurances of your IT department, routine testing finds the overlooked threat posed by the addition of new hardware or software. For example, what about the connectivity of your office printers – they’re live data stores sitting on your network and potentially visible to any person with a web browser?
With all of the above in place, the human factor remains. While computers can be predictable, your staff are often unfamiliar with all of the threats and potential errors. In many organisations, it is not uncommon for 90% of staff to admit to sending an email to an unintended recipient within the preceding year.
Detect: recognise your security events
Security demands that you can detect security events that affect the systems that process personal data, and that you monitor authorised user access to that data. This requires that you can detect anomalous user activity.
You must record user interactions with personal data, and where unexpected events or indications of a personal data breach are detected, you require processes in place to act upon those events as necessary and within an appropriate timeframe.
Minimise: control the impact of an event
It is incumbent upon the organisation to have a structured approach to managing incidents which involve personal data.
In respect of data breaches, you may be required to notify the Information Commissioner’s Office (the ICO), the NCSC, the Action Fraud team or other regulators (such as the Solicitors Regulatory Authority, if you are a law firm). Additional reporting may also be required to the individual(s) affected by the data breach.
How your organisation approaches such events is crucially important: remember that any breach which must be reported to the ICO is required to be submitted within 72 hours of discovery, and failure to do so can result in the risk of €10m fines or 2% of turnover.
While evaluating the event, attention must be devoted to establishing what measures, if any, might be taken to minimise the impact upon the affected individual(s).
Where the loss of availability of personal data could cause harm, these will require that you have measures in place to ensure appropriate recovery. This should include maintaining (and securing) appropriate backups and other elements of a comprehensive disaster recovery plan.
Have you read:
- The Relationship Between GDPR and Cyber Security
- The 5 Hidden Risks of File Sharing
- 10 Step Guide to Cyber Security
- Cyber Security vs. Printers and the IoT
- 12 Cyber Security Readiness Tips
- Cyber Security: Integrating Risk and the CIA Triad
- Why Understanding RISK is Central to Cyber Security
- A GDPR Centred Approach to Cyber Security

⏱ 5 second summary
Part of our Cyber Security Series
Accountability, desired outcomes and risk are essential components of a GDPR-centred approach to cyber security
Recent Posts
Humperdinck Jackman
Director of Consulting Services
Humperdinck has a 30-year career spanning Document Management Systems (DMS), data protection, Artificial Intelligence, Data Protection and Robotic Process Automation. With many articles published in print internationally, he believes the advances in office technology are such that we're entering the 4th Industrial Revolution. Now Director of Marketing and Consulting Services at Advanced UK, he's as active with clients as he is in endeavouring to write original blog articles.


